Crypto
题目给了密文和公钥:enc.message、pub.key
首先需要从公钥里提取modulus,这里使用RsaCtfTool工具(https://github.com/Ganapati/RsaCtfTool)
具体使用方法参考其README
从公钥里dump出n和e:
root@automne:/Pentest/RsaCtfTool# python2.7 RsaCtfTool.py --dumpkey --key ../CTF/UUCTF/pub.key
[*] n: 163325259729739139586456854939342071588766536976661696628405612100543978684304953042431845499808366612030757037530278155957389217094639917994417350499882225626580260012564702898468467277918937337494297292631474713546289580689715170963879872522418640251986734692138838546500522994170062961577034037699354013013
[*] e: 65537
然后直接编辑sage代码,p和q的分解过程已省略:
1 | #!/usr/bin/env sage |
上面脚本的打印内容为:
8096641587229186894277585153143445431328658469873578569106377852712414707527131587696704875863401833093825333228750059921203683371426808985592822234104602514612635325399345655315256059770487262746297969493191875577472710305412454116760400912860976164381975560791496420790885321325002168813949702163950602
但是这里直接Decimal转Hex,再Hex转Ascii是没有可读flag内容的
还是要先转一下Hex:
2F3A14E6673835E94162278A7D846ECEA0F02B51778A1E38019A5DFD3E37D45DEE1F1E3266AAE9A4BB35682F6B28A8D4C3404B3C18FB45BDAD7FBF3945FB2E2DB8A0CD22D44ABA1A2D06675756FB85FB0446EB42B83CAAA14BEEDC6B881BB4DB00053476C6C636C3970633352665A475670626D5666526D78685A32646C0A
但是直接转decode会提示Odd-length string
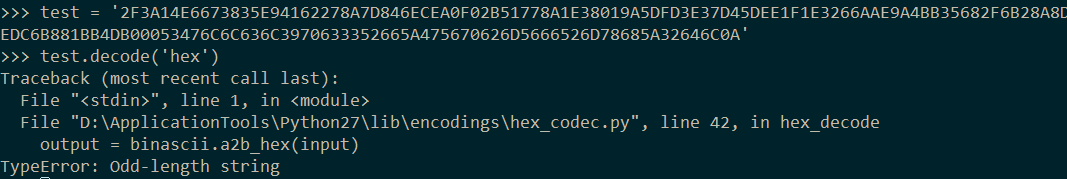
在Hex串前添加0,再decode
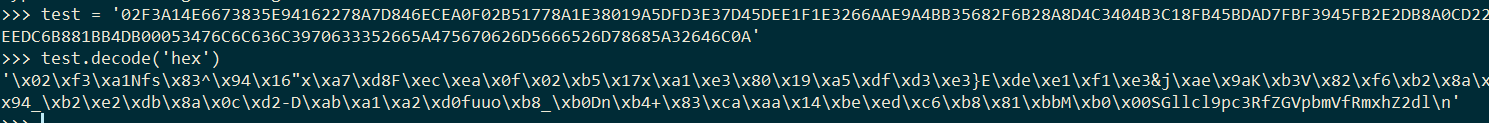
可以看到字符串最后有一段疑似base64的字符串:
SGllcl9pc3RfZGVpbmVfRmxhZ2dl
解码后得到flag:
>>> base64.b64decode("SGllcl9pc3RfZGVpbmVfRmxhZ2dl")
'Hier_ist_deine_Flagge'